Spaghetti: A Website Applications Security Scanner
About Spaghetti
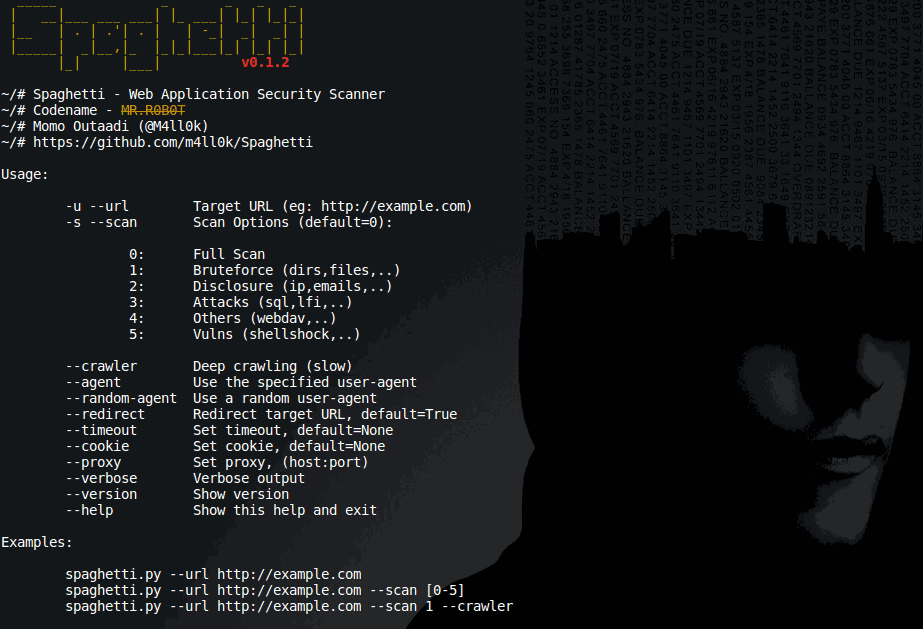
Author: m4ll0k Spaghetti is an Open Source web application scanner, it is designed to find various default and insecure files, configurations, and misconfigurations. Spaghetti is built on Python 2.7 and can run on any platform which has a Python environment.
Spaghetti Installation:
Spaghetti's Features:
Fingerprints:
- Server:
- Web Frameworks (CakePHP,CherryPy,...)
- Web Application Firewall (Waf)
- Content Management System (CMS)
- Operating System (Linux,Unix,..)
- Language (PHP,Ruby,...)
- Cookie Security
- Bruteforce:Admin Interface
Common Backdoors
Common Backup Directory
Common Backup File
Common Directory
Common FileLog File - Disclosure: Emails, Private IP, Credit Cards
- HTML Injection
- SQL Injection
- LDAP Injection
- XPath Injection
- Cross Site Scripting (XSS)
- Remote File Inclusion (RFI)
- PHP Code Injection
- HTTP Allow Methods
- HTML Object
- Multiple Index
- Robots Paths
- Web Dav
- Cross Site Tracing (XST)
- PHPINFO
- .Listing
- ShellShock
- Anonymous Cipher (CVE-2007-1858)
- Crime (SPDY) (CVE-2012-4929)
- Struts-Shock
python spaghetti --url example.com --scan 0 --random-agent --verboseRead more
- Hacker Hardware Tools
- Growth Hacker Tools
- What Is Hacking Tools
- Nsa Hacker Tools
- Pentest Tools Apk
- Hack Tools For Mac
- Tools For Hacker
- Hacker Tools Free Download
- Hack And Tools
- Pentest Tools Nmap
- Hack Rom Tools
- Hacker Tools Apk
- Hacker Tools Free
- Hacking Tools For Pc
- Hacking Tools
- Hacks And Tools
- Pentest Tools Url Fuzzer
- Hacker Tools Software
- Hacker Tools List
- Hacker Techniques Tools And Incident Handling
- Nsa Hack Tools Download
- Hacking Tools Software
- Hacking Tools Hardware
- Hacking Tools Windows
- Hacking Tools Windows
- Hacking Tools Free Download
- Hacking Tools Mac
- Wifi Hacker Tools For Windows
- Easy Hack Tools
- Pentest Tools Open Source
- Hacking Tools Pc
- Hack Tools 2019
- Hacker Tools For Pc
- Hacker Tools Apk Download
- Hacker Tools For Ios
- Hack Tools For Games
- Ethical Hacker Tools
- Hacker
- Hacker Tools Free
- Game Hacking
- Pentest Tools Download
- Termux Hacking Tools 2019
- Wifi Hacker Tools For Windows
- Hacking Tools For Kali Linux
- Hacking Tools 2020
- Computer Hacker
- Hacking Tools For Windows
- Hacking Tools For Windows
- Hack Website Online Tool
- Nsa Hacker Tools
- Hacking App
- Hack Tools For Mac
- Hacking Tools For Beginners
- Wifi Hacker Tools For Windows
- Hack Tools Mac
- World No 1 Hacker Software
- Computer Hacker
- Hacks And Tools
- Pentest Tools For Ubuntu
- Nsa Hacker Tools
- Hackrf Tools
- Hack Website Online Tool
- Pentest Tools Port Scanner
- Hacker Techniques Tools And Incident Handling
- Hacker Tools 2019
- Nsa Hacker Tools
- Hacker Tools For Ios
- Tools For Hacker
- How To Make Hacking Tools
- Pentest Tools Tcp Port Scanner
- Hacks And Tools
- Android Hack Tools Github
- Pentest Automation Tools
- Termux Hacking Tools 2019
- Hacker
- Hacker Tools Apk Download
- Pentest Tools Free
- Hack Tools For Mac
- Hacker Tools List
- Pentest Tools Github
- Pentest Tools For Mac
- Blackhat Hacker Tools
- Wifi Hacker Tools For Windows
- Tools For Hacker
Change Passwords Regularly - A Myth And A Lie, Don'T Be Fooled, Part 1
TL;DR: different passwords have different protection requirements, and different attackers using various attacks can only be prevented through different prevention methods. Password security is not simple. For real advise, checking the second post (in progress).
Are you sick of password advices like "change your password regularly" or "if your password is password change it to pa$$w0rd"? This post is for you!
The news sites are full of password advises nowadays due to recent breaches. When I read/watch these advise (especially on CNN), I am usually pissed off for a lot of reasons. Some advises are terrible (a good collection is here), some are good but without solutions, and others are better, but they don't explain the reasons. Following is my analysis of the problem. It works for me. It might not work for you. Comments are welcome!
Password history
Passwords have been used since ancient times.Because it is simple. When I started using the Internet, I believe I had three passwords. Windows login, webmail, and IRC. Now I have ~250 accounts/passwords to different things, like to my smartphone, to my cable company (this password can be used to change the channels on the TV), to my online secure cloud storage, to full disk encryption to start my computer,
Now, after this lengthy prologue, we will deep dive into the analysis of the problem, by checking what we want to protect, against whom (who is the attacker), and only after that, we can analyze the solutions. Travel with me, I promise it will be fun! ;)
What to protect?
Internet banking, online money
Credit card data
And sometimes, you are your own worst enemy. Don't do stupid things like this:
Work related passwords (e.g. Windows domain)
Email, social sites (Gmail/Facebook/Twitter), cloud storage, online shopping
They can use your account in Facebook votes. Your e-mail, cloud storage is again very important. 20 years ago you also had letters you didn't want to print and put in front of the nearest store, neither want you to do that with your private photo album. On a side note, it is best to use a cloud storage where even the cloud provider admin can't access your data. But in this case, with no password recovery option, better think about "alternative" password recovery mechanisms.
Other important stuff with personal data (e.g. your name, home address)
Not important stuff
This is the category other. I usually use one-time disposable e-mail to these services. Used for the registration, get what I want, drop the email account. Because I don't want to spread my e-mail address all over the internet, whenever one of these sites get hacked. But still, I prefer to use different, random passwords on these sites, although this is the "low level password" class.Attackers and attack methods
After categorizing the different passwords to be protected, let's look at the different attackers and attack methods. They can/will/or actively doing it now:Attacking the clear text password
This is the most effective way of getting the password. Bad news is that if there is no other factor of protection, the victim is definitely not on the winning side. The different attack methods are:- phishing sites/applications,
- social engineering,
- malware running on the computer (or in the browser),
- shoulder surfing (check out for smartphones, hidden cameras),
- sniffing clear-text passwords when the website is not protected with SSL,
- SSL MiTM,
- rogue website administrator/hacker logging clear text passwords,
- password reuse - if the attacker can get your password in any way, and you reuse it somewhere else, that is a problem,
- you told your password to someone and he/she will misuse it later,
- hardware keyloggers,
- etc.
The key thing here is that no matter how long your passwords are, no matter how complex it is, no matter how often do you change it (except when you do this every minute ... ), if it is stolen, you are screwed. 2FA might save you, or might not.
Attacking the encrypted password
This is the usual "hack the webserver (via SQL injection), dump the passwords (with SQLMap), post hashes on pastebin, everybody starts the GPU farm to crack the hashes" scenario. This is basically the only scenario where the password policies makes sense. In this case the different level of passwords need different protection levels. In some cases, this attack turns out to be the same as the previous attack, when the passwords are not hashed, or are just encoded.The current hash cracking speeds for hashes without any iterations (this is unfortunately very common) renders passwords like Q@tCB3nx (8 character, upper-lowercase, digit, special characters) useless, as those can be cracked in hours. Don't believe me? Let's do the math.
Let's say your password is truly random, and randomly choosen from the 26 upper, 26 lower, 10 digit, 33 special characters. (Once I tried special passwords with high ANSI characters inside. It is a terrible idea. Believe me.). There are 6 634 204 312 890 620 different, 8 character passwords from these characters. Assuming a 2 years-old password cracking rig, and MD5 hash cracking with 180 G/s speed, it takes a worst case 10 hours (average 5) to crack the password,
A lot of common hashing algorithms don't use protections against offline brute-force attacks. This includes LM (old Windows hashes), NTLM (modern Windows hashes), MD-5, SHA1-2-512. These hashing algorithms were not developed for password hashing. They don't have salting, iterations, etc. out of the box. In the case of LM, the problem is even worse, as it converts the lowercase characters to uppercase ones, thus radically decreasing the key space. Out of the box, these hashes are made for fast calculation, thus support fast brute-force.
Another attack is when the protected thing is not an online service, but rather an encrypted file or crypto-currency wallet.
Attacking the authentication system online
Attacking single sign on
Attacking 2FA
- one time tokens (SecurID, Yubikey) can be relayed in a man-in-the-middle attack,
- smartcard authentication can be relayed with the help of a malware to the attacker machine - or simply circumvented in the browser malware,
- text based (SMS) messages can be stolen by malware on the smartphone or rerouted via SS7,
- bio-metric protection is constantly bypassed,
- SSH keys are constantly stolen,
- but U2F keys are pretty good actually, even though BGP/DNS hijack or similar MiTM can still circumvent that protection,
- etc.
Others
Beware that there are tons of other attack methods to access your online account (like XSS/CSRF), but all of these have to be handled on the webserver side. The best you can do is to choose a website where the Bug Bounty program is running 24/7. Otherwise, the website may be full of low hanging, easy-to-hack bugs.Now that we have covered what we want to protect against what, in the next blog post, you will see how to do that. Stay tuned. I will also explain the title of this blog post.Read more
- New Hacker Tools
- Pentest Tools Subdomain
- Nsa Hack Tools Download
- Hacking Tools For Windows Free Download
- Hack Tool Apk No Root
- Hacking Tools For Windows
- New Hack Tools
- Hacking Apps
- Bluetooth Hacking Tools Kali
- Hack App
- Pentest Tools Android
- Tools Used For Hacking
- Best Pentesting Tools 2018
- Hacker Security Tools
- Pentest Automation Tools
- Hacking Tools Download
- Hack Tools 2019
- Pentest Automation Tools
- Android Hack Tools Github
- Hacking Tools For Windows 7
- Hack Tools Download
- How To Install Pentest Tools In Ubuntu
- Computer Hacker
- Pentest Tools For Ubuntu
- Hacking Tools Windows 10
- Hak5 Tools
- Hackers Toolbox
- Game Hacking
- Hacker Techniques Tools And Incident Handling
- Hack Tools For Windows
- Pentest Tools Android
- Pentest Tools Windows
- Best Hacking Tools 2019
- Pentest Box Tools Download
- Pentest Tools Nmap
- Kik Hack Tools
- Beginner Hacker Tools
- Hack Tools For Mac
- Pentest Tools Linux
- Bluetooth Hacking Tools Kali
- Tools Used For Hacking
- What Are Hacking Tools
- Hacking Tools
- Hacker Hardware Tools
- Hacker Tools For Ios
- How To Hack
- Termux Hacking Tools 2019
- Hacking Tools Online
- Pentest Tools Port Scanner
- Hack Tools Mac
- Pentest Tools Bluekeep
- Hacker Tools
- Best Hacking Tools 2020
- Pentest Tools Find Subdomains
- Kik Hack Tools
- Hacks And Tools
- How To Make Hacking Tools
- Top Pentest Tools
- Hacking Tools 2020
- Hack Tool Apk No Root
- Hack Tools For Windows
- Pentest Tools For Windows
- Wifi Hacker Tools For Windows
- Hacking Tools Mac
- Wifi Hacker Tools For Windows
- Pentest Tools Review
- Hack Tools 2019
- Hacking Tools For Windows
- New Hacker Tools
- Pentest Tools Website
- Pentest Recon Tools
- Underground Hacker Sites
- Pentest Tools Online
- Hacker Tools For Pc
- Hacking Tools For Windows
- Tools For Hacker
- Hacking Tools Online
- Tools 4 Hack
- Nsa Hack Tools Download
- Hacker Tools Apk Download
- Pentest Box Tools Download
- Pentest Tools Subdomain
- Hacker Tools For Pc
- Pentest Tools For Windows
- Hack Tools 2019
- Hacking Tools For Windows
- Hacking App
- Hacking Tools Name
- Nsa Hack Tools Download
- Pentest Tools Alternative
Experts Reported Security Bug In IBM's Db2 Data Management Software
Cybersecurity researchers today disclosed details of a memory vulnerability in IBM's Db2 family of data management products that could potentially allow a local attacker to access sensitive data and even cause a denial of service attacks. The flaw (CVE-2020-4414), which impacts IBM Db2 V9.7, V10.1, V10.5, V11.1, and V11.5 editions on all platforms, is caused by improper usage shared memory,
via The Hacker News
More info
- Wifi Hacker Tools For Windows
- Hack Tools
- Pentest Tools Website
- Bluetooth Hacking Tools Kali
- Pentest Tools Bluekeep
- Hacker Search Tools
- Pentest Tools Subdomain
- Pentest Tools Apk
- Pentest Tools For Ubuntu
- Pentest Tools Tcp Port Scanner
- Tools For Hacker
- Best Hacking Tools 2019
- Hacker Tools 2020
- Hacker Tool Kit
- Hack Tools For Games
- Hacker Tools Free
- Pentest Box Tools Download
- Pentest Reporting Tools
- Computer Hacker
- Tools For Hacker
- Hacking Tools Windows
- Pentest Tools For Windows
- Hack Tool Apk
- Tools 4 Hack
- Underground Hacker Sites
- Easy Hack Tools
- Nsa Hacker Tools
- Hacking Tools And Software
- Hacker Tools Free Download
- Pentest Tools Linux
- Hack Tools Pc
- Pentest Tools Online
- Best Hacking Tools 2020
- Hacking Tools 2019
- Hack Tools Download
- Pentest Tools Open Source
- Hack App
- Hacking Tools 2020
- Hacker Tools Apk
- Hack Website Online Tool
- Pentest Tools Free
- Pentest Tools Open Source
- Pentest Reporting Tools
- Pentest Tools Windows
- Hack Website Online Tool
- Hacker Tools Free Download
- Pentest Tools Open Source
- Hack Tools For Ubuntu
- Ethical Hacker Tools
- Top Pentest Tools
- Hacker Tools For Mac
- Tools 4 Hack
- Hacker Tool Kit
- Pentest Tools For Android
- Nsa Hacker Tools
- Hacking Tools Windows 10
- Hack Tools For Games
- Pentest Tools Open Source
- Kik Hack Tools
- Hacker Search Tools
- Hack And Tools
- Best Hacking Tools 2020
- Pentest Tools
- Hacker Tools Windows
- Hack Rom Tools
- Underground Hacker Sites
- Game Hacking
- Hacking Tools 2020
- Hack Tools Github
- What Is Hacking Tools
- Hacker Tools For Mac
- Game Hacking
- Github Hacking Tools
- Hacking Tools Name
- Hack Tools For Ubuntu
- Pentest Tools Online
- Kik Hack Tools
- How To Make Hacking Tools
- Pentest Tools Review
- Hack Tools
- Github Hacking Tools
- Hacking Tools Software
- Hacking Tools
- Hacking App
- Pentest Tools List
- What Are Hacking Tools
- Bluetooth Hacking Tools Kali
- Hacker Tools Free Download
- Black Hat Hacker Tools
- What Is Hacking Tools
- Hacker Tools Linux
- Hacker Tools Mac
- Hack Tools
- Pentest Tools Free
- Hacker Techniques Tools And Incident Handling
- New Hacker Tools
- Hackers Toolbox
- Hak5 Tools
- Hacker Security Tools
- Nsa Hacker Tools
- Tools Used For Hacking
- Hack Tools For Ubuntu
- Hacking Tools And Software
- Hacker Tools Apk
- Hack Apps
- Hacker Tools Apk
- Hacker Tools Linux
- Hack Tools
- Computer Hacker
- Hacking Tools For Pc
- Underground Hacker Sites
- Hacker Techniques Tools And Incident Handling
- World No 1 Hacker Software
- Hacking Tools For Mac
- Install Pentest Tools Ubuntu
- Hacker Hardware Tools
- Hacking Tools Usb
- Hacking Apps
- Hacker Tools Windows
- Hack Apps
- What Is Hacking Tools
- Hacks And Tools
- Hacker Security Tools
- Pentest Tools Website Vulnerability
- Hacker Tool Kit
- Pentest Tools Online
- Top Pentest Tools
- Hacking Tools For Pc
- Hack Tools Github
- Hacking Tools Name
- Hacker Hardware Tools
- Pentest Recon Tools
- Hacking Tools Usb
- Hack And Tools
- Pentest Tools Review
- Hacker Tools Windows
- Nsa Hack Tools
- Hacker Tools List
- Pentest Tools Linux
- Hacker Tools Apk Download
PentestBox - Opensource PreConfigured Portable Penetration Testing Environment For The Windows
Related word
- Hacker Tools Mac
- Pentest Tools Open Source
- New Hacker Tools
- Pentest Tools Review
- Hacking Tools Software
- Pentest Tools Online
- Pentest Tools
- Computer Hacker
- Hacker Tools Free Download
- Hack Tools For Ubuntu
- Game Hacking
- Hacker Tools For Pc
- Top Pentest Tools
- What Are Hacking Tools
- Hacking Tools Online
- Pentest Tools Github
- Hacker Tools Hardware
- Hacker Tools List
- Wifi Hacker Tools For Windows
- Hacker Tools Free
- Pentest Tools Github
- Beginner Hacker Tools
- Pentest Tools Android
- Pentest Tools For Ubuntu
- Hacker Tools Mac
- Hacking Tools Github
- Hacker Tools 2019
- Hacking Tools Online
- Hacker Tools Online
- Android Hack Tools Github
- Android Hack Tools Github
- Free Pentest Tools For Windows
- Pentest Tools Apk
- Hacking App
- Hacking Tools For Beginners
- What Are Hacking Tools
- Nsa Hacker Tools
- Hack And Tools
- Pentest Tools Port Scanner
- Hacker Tools For Mac
- Hack Tools
- Hack Tools Github
- Hacker Tools Mac
- Pentest Tools Framework
- Hacking Tools For Windows
- Hacker Tools List
- Install Pentest Tools Ubuntu
- Wifi Hacker Tools For Windows
- Hack Tools Pc
- Hacker Tools Github
- Pentest Tools Find Subdomains
- Usb Pentest Tools
- Pentest Tools Url Fuzzer
- Hacker Tools Mac
- Pentest Tools Framework
- Hacking Tools And Software
- Hacker Tools List
- Hack Tool Apk No Root
- Hacker Hardware Tools
- Hacker Tool Kit
- Pentest Tools For Mac
- Pentest Tools For Ubuntu
- What Are Hacking Tools
- Usb Pentest Tools
- Hacker
- Pentest Tools Website Vulnerability
- Hacking Tools Hardware
- Hacker Tools
- Hacking Tools Usb
- How To Install Pentest Tools In Ubuntu
- Hacking Tools For Games
- Easy Hack Tools
- Underground Hacker Sites
- How To Hack
- Usb Pentest Tools
- Hacking Tools Mac
- Pentest Tools For Windows
- Hacking Tools For Windows
- Hack App
- Pentest Tools For Windows
- Pentest Tools List
- Pentest Tools Download
- Tools 4 Hack
- Hacks And Tools
- How To Install Pentest Tools In Ubuntu
- Pentest Tools For Ubuntu
- Hacker Tools
- Hacker Tools 2020
- Hack Tools For Games
- Pentest Tools List
- Pentest Tools Online
- Hacker Hardware Tools
- Pentest Tools Nmap
- Pentest Tools Url Fuzzer
- Pentest Tools Github
- Pentest Tools Review
- Hack Tools For Pc
- How To Make Hacking Tools
- Hack Tools
- Beginner Hacker Tools
- Pentest Tools Apk
- Hack Tools Pc
- Hacker Tools Github
- Pentest Tools Review
- Hacker Tools Free
- Pentest Tools Linux
- Pentest Tools For Android
- Hacker
- Pentest Tools Download
- Hacker Hardware Tools
- Hacker Tools For Ios
- Hacking Tools For Pc
- Hacker Search Tools
- Wifi Hacker Tools For Windows
- Hacker Tools Windows
- Hacking Tools 2019
- Hacker Tools Software
- Hack Tools
- Black Hat Hacker Tools
- Hacker Tool Kit
- Hacking Tools 2020
- Hack Tools For Ubuntu
- Hacking Tools 2020
- Hack And Tools
- Pentest Tools Find Subdomains
- Hack Tools For Games
- World No 1 Hacker Software
- Pentest Box Tools Download
- Hack Tools For Windows
- Hacker Tools For Windows
- Hacking Tools
- Pentest Tools Online
- Hacker Tools Online
- Hacking Tools Mac
- Pentest Tools Tcp Port Scanner
- Hacking App
- Hackers Toolbox
- What Are Hacking Tools
- Growth Hacker Tools
- Hacking Tools Usb
- Pentest Tools Review
- Pentest Tools Subdomain
- Pentest Tools Apk
- Hacker Tools For Windows
- Install Pentest Tools Ubuntu
- Pentest Tools Open Source
- Pentest Tools For Android
- Best Hacking Tools 2019
- Pentest Tools Framework
- Pentest Tools Subdomain
- Hack Tools
- Pentest Tools Kali Linux
- Hacker Tools 2019